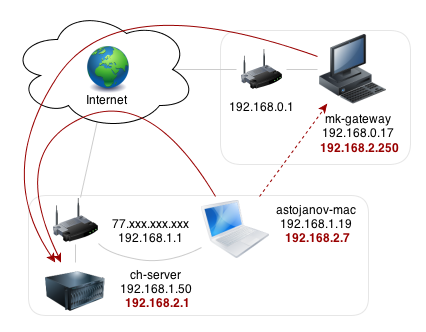
Port Redirection over VPN to a host on the remote network

Routers support open port to a host on the remote network as long as the VPN tunnel established. Clients from the Internet can access specific ports through the WAN interface of the VPN support router, and the router will forward the traffic over the VPN to the remote network. It’s the solution to allow internet access to the servers or resources on the remote network which doesn’t have a public IP or its ISP blocks certain port.
Here is a scenario where this feature will be very useful. There is a company of which the warehouse in the suburbs, where the fixed-line internet service is not available, the network administrator can only use LTE as the internet source for the warehouse. The LTE only owns a virtual IP address, which makes accessing the surveillance system and inventory management system at the warehouse from the Internet very difficult.
But the company’s office locates downtown, which has the fixed-line and a public IP address. So the network administrator constructs the VPN network between the office and warehouse, then, set up the office router to forward specific ports to the warehouse router. Then, the managers can access the warehouse’s network to check the live footage and inventory information at any places as long as they connect to the Internet.
We provide different range of VPN Products





Protect Your Data via VPN
In the event of data loss, companies can face unpleasant consequences leading to various legal and marketing problems. Economic losses, as severe as complete bankruptcy, are also possible. It is logical to assume that cybersecurity and protection of data is a necessity for all companies that strive for successful functioning.
Initially, companies created VPNs in order to protect the privacy of their employees and corporate data, because the interception of information has been and remains one of the most common means of corporate espionage. Moreover, new ways of intercepting data on the Internet appear regularly. Security experts later discovered the KRACK, which was particularly vulnerable to WiFi networks. However, even before that, hackers already had programs for stealing information such as MAC spoofing, Firesheep, etc.
That is why IT engineers were tasked with creating software that would increase the level of security of Internet connections. As a result, they developed a security program that creates an encrypted connection between two devices.